
ISO/IEC 27400:2022 Cybersecurity — IoT Security and Privacy
In today’s hyper-connected world, the Internet of Things (IoT) has transformed how we live and work. From smart homes to industrial automation, IoT devices have become ubiquitous, driving efficiency and innovation. However, this interconnectedness also introduces significant cybersecurity risks. Recognizing the need for robust security measures, the ISO/IEC 27400:2022 standard provides comprehensive guidelines for IoT security and privacy.
ISO/IEC 27400 offers a structured framework to safeguard IoT systems against cyber threats and ensure the privacy of data. This standard addresses a wide range of security aspects, including device integrity, data protection, and network security, making it indispensable for organizations leveraging IoT technology.
If you’re seeking certification for ISO/IEC 27400:2022, contact us at support@pacificcert.com or call +91-8595603096. Our team at Pacific Certifications is ready to assist you!
What are the Requirements of ISO/IEC 27400:2022?
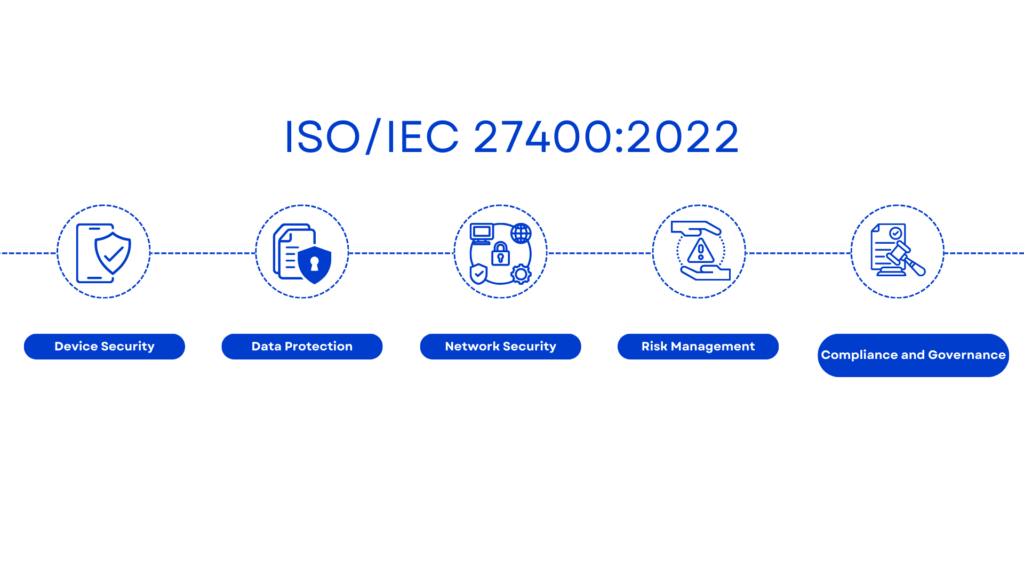
Implementing ISO/IEC 27400 involves meeting several critical requirements to ensure comprehensive IoT security and privacy. These requirements are designed to address various aspects of IoT systems, from device security to data protection. Here are the key requirements:
Device Security
- Authentication and Authorization: Ensure that only authorized users and devices can access IoT systems.
- Firmware Integrity: Regularly update and verify device firmware to protect against vulnerabilities.
- Physical Security: Implement measures to prevent unauthorized physical access to IoT devices.
Data Protection
- Encryption: Encrypt data both at rest and in transit to prevent unauthorized access.
- Data Minimization: Collect and retain only the necessary data to reduce privacy risks.
- Anonymization and Pseudonymization: Use techniques to anonymize or pseudonymize data to protect user privacy.
Network Security
- Secure Communication Protocols: Use robust communication protocols to protect data transmission.
- Network Segmentation: Isolate IoT devices from critical networks to limit the impact of a potential breach.
- Intrusion Detection Systems (IDS): Deploy IDS to monitor and respond to suspicious network activities.
Risk Management
- Threat Modelling: Identify potential threats and vulnerabilities in the IoT ecosystem.
- Incident Response Plan: Develop and maintain an incident response plan to address security breaches promptly.
- Continuous Monitoring: Implement continuous monitoring to detect and respond to security incidents in real time.
Compliance and Governance
- Regulatory Compliance: Ensure compliance with relevant regulations and standards.
- Policy Development: Establish and enforce security policies and procedures.
- Training and Awareness: Conduct regular training to educate employees about IoT security best practices.
Need assistance with ISO/IEC 27400:2022 certification? Reach out to us at support@pacificcert.com or give us a call at +91-8595603096 for expert guidance!
What are the Benefits of ISO/IEC 27400:2022?
Adopting ISO/IEC 27400:2022 offers numerous benefits to organizations, enhancing their security posture and fostering trust with stakeholders. Here are some of the key advantages:
Enhanced Security
Implementing ISO/IEC 27400:2022 significantly enhances the security of IoT systems, protecting against a wide range of cyber threats. This standard provides a comprehensive framework to identify and mitigate vulnerabilities, ensuring that IoT devices and data are secure.
Improved Privacy
By adhering to the privacy guidelines outlined in ISO/IEC 27400:2022, organizations can protect sensitive user data and ensure compliance with data protection regulations.
Regulatory Compliance
ISO/IEC 27400:2022 helps organizations meet regulatory requirements and industry standards related to IoT security and privacy.
Operational Efficiency
Implementing the guidelines in ISO/IEC 27400:2022 can streamline security processes and improve operational efficiency.
Competitive Advantage
Organizations that achieve ISO/IEC 27400:2022 certification can differentiate themselves in the marketplace by demonstrating their commitment to cybersecurity.
For more information on ISO/IEC 27400:2022 certification, email us at support@pacificcert.com or phone +91-8595603096. Pacific Certifications is here to help!
Who Needs ISO/IEC 27400:2022?
ISO/IEC 27400:2022 is relevant to a wide range of organizations that utilize IoT technology. Here are some examples of who can benefit from this standard:
Manufacturing
Manufacturing organizations that use IoT for automation and monitoring can benefit from the security and privacy guidelines in ISO/IEC 27400. This standard helps protect industrial control systems and sensitive production data.
Healthcare
Healthcare providers that deploy IoT devices for patient monitoring and medical records management must ensure the security and privacy of patient data. ISO/IEC 27400 provides a framework to safeguard these critical systems.
Smart Cities
Municipalities implementing smart city initiatives can use ISO/IEC 27400:2022 to protect critical infrastructure and citizen data. This standard helps ensure the security of IoT devices used in transportation, energy management, and public safety.
Consumer Electronics
Manufacturers of consumer IoT devices, such as smart home gadgets, can adopt ISO/IEC 27400:2022 to enhance the security and privacy of their products.
Telecommunications
Telecommunications companies that provide IoT services can benefit from ISO/IEC 27400:2022 by ensuring the security of their networks and customer data.
How We Can Help
Pacific Certifications is a leading certification body specializing in ISO standards. We can assist your organization with the audit and certification process for ISO/IEC 27400:2022.
Our expert auditors have extensive experience in IoT security and privacy. We follow a thorough and systematic approach to ensure that your organization meets all the requirements of ISO/IEC 27400:2022. Our certification services provide you with the assurance that your IoT systems comply with the highest standards of security and privacy.
Interested in getting certified for ISO/IEC 27400:2022? Contact us at support@pacificcert.com or call +91-8595603096. Pacific Certifications will guide you through the process.
Why Choose Pacific Certifications?
- Expert Auditors: Our auditors possess deep knowledge of IoT security and privacy standards.
- Comprehensive Audits: We conduct detailed audits to ensure full compliance with ISO/IEC 27400:2022.
- Reliable Certification: Our certification process is transparent, rigorous, and trustworthy.
- Global Recognition: Certifications issued by Pacific Certifications are recognized worldwide, enhancing your organization’s credibility.
What is the Certification Process?
Achieving ISO/IEC 27400:2022 certification involves several steps, each designed to ensure that your organization meets the required standards. Here is an overview of the certification process with Pacific Certifications:
Initial Inquiry: Contact us to discuss your certification needs. We will provide detailed information about the certification process and requirements.
Application: Submit your application for certification, including necessary documentation about your IoT systems and security measures.
Pre-Audit Assessment: Our auditors will conduct a pre-audit assessment to identify any potential gaps and areas for improvement.
Formal Audit: The formal audit involves a thorough evaluation of your IoT systems, policies, and procedures against the ISO/IEC 27400:2022 standards.
Audit Report: After the audit, we will provide a detailed report highlighting any non-conformities and recommendations for corrective actions.
Corrective Actions: Implement the recommended corrective actions to address any identified gaps.
Certification Decision: Once all non-conformities are resolved, we will make a certification decision and issue the ISO/IEC 27400:2022 certificate.
Surveillance Audits: Periodic surveillance audits will be conducted to ensure ongoing compliance with the standard.
Achieve ISO/IEC 27400 certification with Pacific Certifications and ensure the highest standards of IoT security and privacy for your organization. Contact us today to begin your certification journey and enhance your cybersecurity posture!
For more information or to start your certification process, please reach out to us at:
Email: support@pacificcert.com
Phone: +91-8595603096
FAQS: ISO/IEC 27400:2022
ISO/IEC 27400 is a standard that provides guidelines for IoT security and privacy. It addresses various aspects of IoT systems, including device security, data protection, and network security.
Organizations across various sectors, including manufacturing, healthcare, smart cities, consumer electronics, and telecommunications, can benefit from implementing ISO/IEC 27400.
The standard enhances security by providing comprehensive guidelines for authenticating devices, protecting data, securing networks, and managing risks associated with IoT systems.
Pacific Certifications provides audit and certification services for ISO/IEC 27400. We ensure that your organization meets all the requirements of the standard through our rigorous and transparent certification process.
The certification process includes an initial inquiry, application submission, pre-audit assessment, formal audit, audit report, corrective actions, certification decision, and periodic surveillance audits.
ISO/IEC 27400 is important because it provides a structured approach to securing IoT systems and protecting data privacy. Implementing this standard helps organizations mitigate cybersecurity risks and comply with regulatory requirements.
Pacific Certifications is accredited by ABIS, in case you need support with ISO/IEC 27400:2022 for your business, please contact us at support@pacificcert.com or +91-8595603096.
Also Read: ISO/IEC TS 27560:2023 Privacy Technologies







