What is ISO/IEC 27001:2022?

ISO/IEC 27001:2022 is the latest version of the globally recognized standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Published by ISO and IEC, this standard sets a systematic foundation to manage sensitive data, prevent cyber threats and ensure confidentiality, integrity, and availability of information.
Designed for organizations of all sizes and across industries, ISO 27001:2022 enables a proactive approach to information risk management. Whether you handle customer data or intellectual property, certification to this standard shows your dedication to data security and compliance.
The 2022 revision of ISO/IEC 27001 reflects modern cybersecurity challenges and includes a significant update to Annex A controls to align with ISO/IEC 27002. It incorporates cloud security, remote working, threat intelligence, and data masking etc, making it highly relevant in today’s digital landscape.
If your organization handles sensitive data and aims to get certified according to ISO/IEC 27001:2022, contact us at support@pacificcert.com.
Purpose
The primary goal of ISO 27001 is to help organizations build and maintain an effective ISMS that protects critical information assets. This is done through a risk-based methodology, requiring identification, analysis, treatment, and monitoring of security risks. The 2022 revision aligns the standard with evolving cybersecurity trends and digital transformation needs. ISO 2700 helps organizations to secure data through a proactive, continuous improvement approach (Plan-Do-Check-Act).
Scope and Applicability
Scope:
ISO/IEC 27001:2022 is applicable to any organization, regardless of size, sector, or geographical location, that needs to protect information assets. It covers all types of data, digital, paper-based, or verbal and applies to internal systems, suppliers, cloud environments, and outsourced services.
Applicability:
- IT and software companies
- Financial institutions and fintech firms
- Healthcare and pharmaceutical organizations
- Government and public sector entities
- E-commerce and cloud service providers
- Legal, consulting, and professional service firms
Whether you’re a multinational corporation or a small enterprise, ISO/IEC 27001:2022 can be customized to address your specific information security needs, contact us at support@pacificcert.com to know more!
Key Definitions
- Information Security: The preservation of confidentiality, integrity, and availability of information
- ISMS: A set of interrelated policies and procedures to manage information security risks
- Risk Assessment: The process of identifying and evaluating security risks to information assets
- Annex A Controls: A catalogue of security controls (now 93 in the 2022 version) that organizations can implement based on risk and context
- SoA (Statement of Applicability): A document that lists which controls are applicable to the organization and why
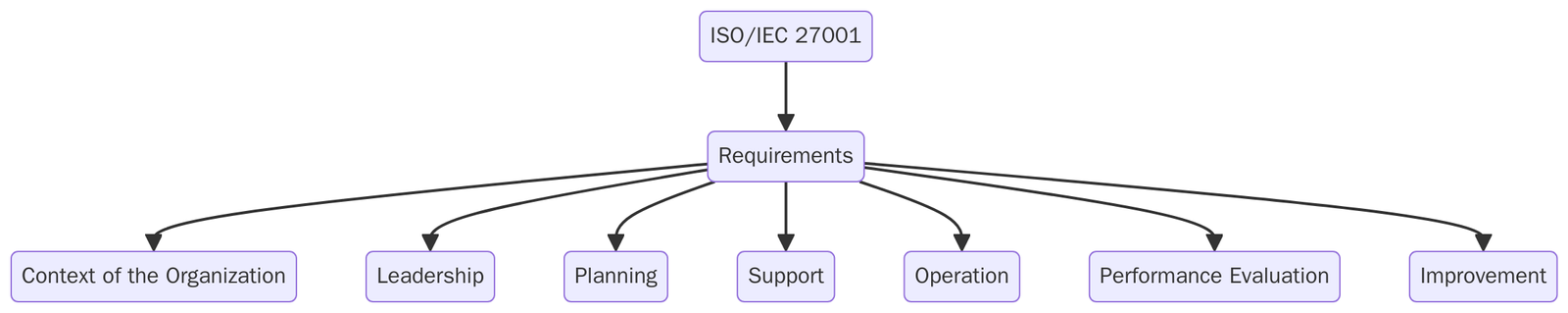
ISO 27001 Clauses – Wise Structure
ISO 27001 clauses are organized into 10 clauses, which provide the structural framework for implementing and maintaining an effective ISMS:
Clause | Title | Purpose |
1 | Scope | Defines the standard’s boundaries and applicability. |
2 | Normative References | Lists referenced standards essential for implementation. |
3 | Terms and Definitions | Provides a glossary to ensure common understanding. |
4 | Context of the Organization | Understands internal/external factors and stakeholder expectations. |
5 | Leadership | Establishes top management commitment, ISMS roles, and information security policy. |
6 | Planning | Conducts risk assessment, determines risk treatment options, and sets measurable objectives. |
7 | Support | Addresses resource allocation, awareness, communication, and documentation control. |
8 | Operation | Implements risk treatment plans and manages operational processes. |
9 | Performance Evaluation | Involves monitoring, internal audits, and management reviews. |
10 | Improvement | Handles nonconformities and drives continual improvement. |
Annex A – Updated Controls in ISO 27001:2022
Annex A in the 2022 version categorizes 93 controls into four high-level themes, replacing the previous 14 domains and better reflecting modern information security challenges. The new controls cover areas such as threat intelligence, cloud services security, ICT readiness for business continuity, physical security monitoring, configuration management, secure coding, data masking, data leakage prevention, web filtering, and monitoring activities:
Theme | No. of Controls | Examples |
Organizational Controls | 37 | Policies, roles, supplier relationships, threat intelligence |
People Controls | 8 | Background checks, user responsibilities, awareness training |
Physical Controls | 14 | Equipment security, secure areas, physical access controls |
Technological Controls | 34 | Encryption, data masking, logging, monitoring, endpoint protection |
Controls such as threat intelligence, data leakage prevention, web filtering, and secure coding are new additions that reflect emerging cyber risks.
Transition Timeline: Organizations currently certified to ISO 27001:2013 will need to transition to ISO 27001:2022 by the end of October 2025 to maintain a valid certification. The official transition period spans three years from the new standard’s publication (which was October 2022). After October 31, 2025, certificates issued against the 2013 edition will expire or be withdrawn
ISO 27001 Requirements
Implementation of ISMS involves establishing or updating security policies and procedures, implementing necessary technical controls, conducting staff training and awareness, and embedding risk management practices into business processes. You will need to define the scope of your ISMS and perform a formal risk assessment to determine which threats and vulnerabilities require mitigation. For each risk, you’ll apply appropriate controls from ISO 27001’s Annex A or other measures and document the rationale in a Statement of Applicability. Other steps include:
- After the risk assessment and treatment process, identify and mitigate vulnerabilities.
- Develop an ISMS policy and assign information security roles and responsibilities.
- Implement relevant Annex A controls and document the Statement of Applicability (SoA).
- Ensure employee training, awareness, and secure information handling practices.
- Conduct internal audits, management reviews, and performance evaluations.
- Document policies, procedures, and logs to support transparency and compliance.
- Establish a culture of continuous improvement in information security.
Documentation Required
If you have already implemented the ISO 27001 standard, you will be requested to get these documents ready for the certification audit:
- ISMS policy and scope statement
- Risk assessment and treatment methodology
- Risk treatment plan and SoA
- Control implementation procedures
- Incident management and response plan
- Access control policy
- Internal audit reports
- Corrective action logs
- Records of training, awareness, and monitoring activities
Benefits of ISO 27001:2022 Certification
ISO/IEC 27001 establishes a systematic approach to managing sensitive information. It ensures the confidentiality, integrity, and availability of data across physical and digital environments
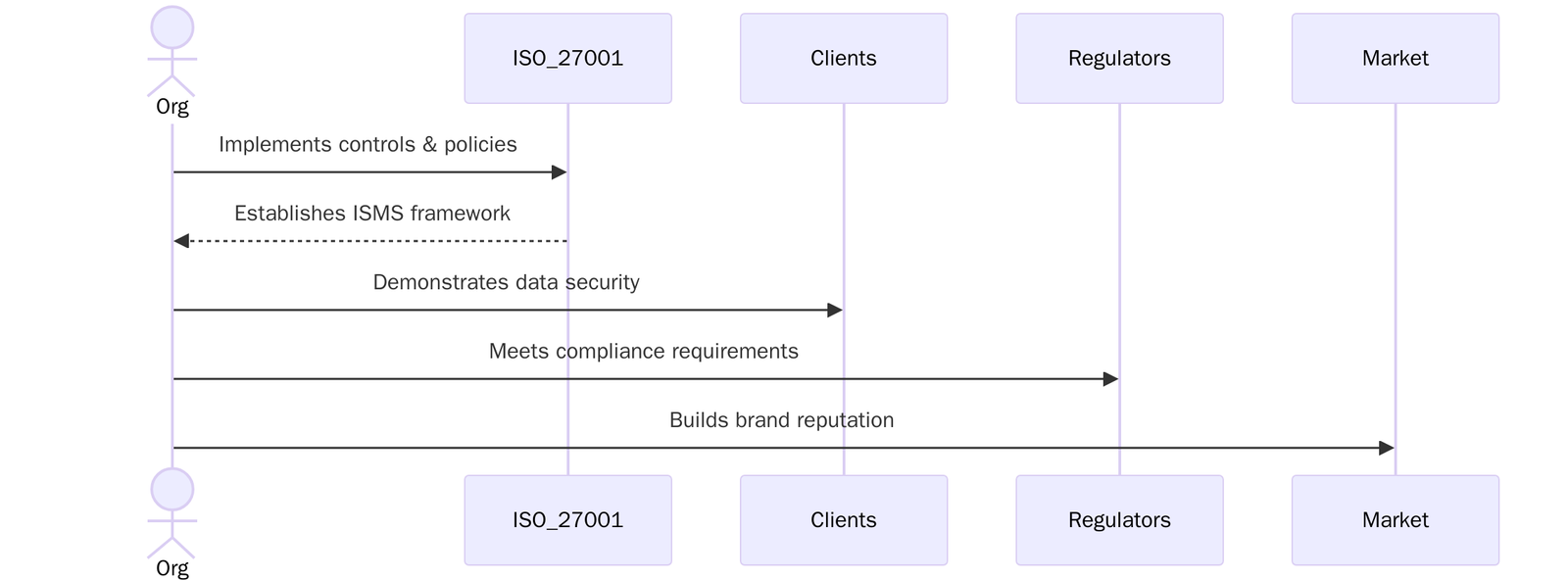
- Protects sensitive data across physical and digital environments by ensuring confidentiality, integrity, and availability are preserved at all times.
- Demonstrates compliance with major global regulations like GDPR, HIPAA, CCPA, and RBI/SEBI, reducing legal exposure and audit risks.
- Builds trust and credibility with customers, partners and regulators by showcasing a certified approach to information security.
- Reduces the risk of data breaches and cyberattacks by implementing a structured, risk-based control framework.
- Enables market access and global expansion by fulfilling mandatory security requirements in international contracts and supply chains.
- Improves resilience and response readiness, ensuring timely detection, response, and recovery from information security incidents.
- Manages third-party and supplier risks through documented processes for vendor access, oversight, and security validation.
- Secures remote and cloud-based operations, supporting today’s hybrid work models, SaaS platforms, and digital transformation strategies.
- Enhances internal governance and accountability, driving a culture of security awareness, ownership, and operational discipline.
- Drives continual improvement through regular monitoring, performance reviews, and corrective actions aligned with evolving threats.
Several key trends why ISO 27001:2022 has become an urgent requirement:
Cyberattacks
According to IBM’s 2024 report, the average cost of a data breach has crossed USD 4.5 million, with ransomware accounting for over 25% of all major incidents. High-profile attacks on supply chains, healthcare systems, and critical infrastructure have forced businesses to adopt structured ISMS frameworks.
Regulatory requirements
New and updated data protection laws across regions, such as GDPR in the EU, CPRA in California, PDPA in Singapore, and India’s Digital Personal Data Protection Act (DPDPA)—now require demonstrable security controls. ISO 27001 certification offers a recognized path to compliance.
Cloud adoption and remote work
Organizations operating in cloud environments or managing hybrid teams face a growing risk surface. ISO 27001 addresses these challenges with updated controls for cloud security, access management, secure coding, and endpoint protection.
Clients and partners now demand certification.
More procurement departments are including ISO 27001:2022 as a mandatory vendor requirement, especially in sectors like fintech, SaaS, telecom, and manufacturing. Having the certificate often determines whether you’re shortlisted for global contracts, tenders, or partnership deals.
How ISO 27001:2022 Helps Organizations?
ISO 27001:2022 gives businesses a clear and organized way to manage information security. Instead of using short-term fixes, it helps you look at the big picture, identifying where your risks are, setting up the right protections, and making sure those protections are working overtime. This approach helps companies to reduce the chances of data breaches, define who is responsible for what, and create a strong culture of security across the team. It’s a flexible standard that works well in any industry.
Getting certified to ISO 27001 shows that your organization takes information security seriously and has the right systems in place to keep data safe.
ISO 27001 Certification Cost
ISO 27001 certification cost varies based on organizational size, scope, and readiness. A well-prepared ISMS reduces time and cost of certification. Below are the factors pricing is based on:
- Size and complexity of the organization
- Scope of ISMS and number of locations/systems covered
- Maturity level of existing policies and security controls
- Readiness for audit (gap assessment may be required)
- Need for integrated audits (e.g., with ISO 9001, ISO 22301)
For a customized quote for ISO/IEC 27001:2022 certification, contact us at support@pacificcert.com
Certification Timeline
The certification process usually takes 8 to 12 weeks, depending on readiness and scope.
Week | Phase | Description |
Week 1 | Application & Initial Assessment | Define scope, objectives, and baseline controls. |
Week 2–4 | Gap Analysis & Documentation Review | Identify nonconformities and prepare required documentation. |
Week 5–6 | Internal Audits & Risk Assessment | Conduct self-audits and formal risk assessment. |
Week 7–8 | Stage 1 Audit (Readiness Review) | Auditor reviews documentation and basic ISMS structure. |
Week 9–10 | Stage 2 Audit (Implementation Review) | Auditor verifies practical implementation and effectiveness. |
Week 11–12 | Final Report & Certification Decision | Certificate issued after corrective actions (if any) are closed. |
ISO 27001:2022 Certification Audit
The ISO 27001:2022 certification audit, conducted by a third party certification body, is a formal and independent review of your organization’s Information Security Management System (ISMS). It evaluates whether your systems, controls, and processes meet the requirements set out in the ISO 27001:2022 standard.
The audit is conducted in two key stages:
Stage 1 – Documentation Review
This is the first step in the audit process. The auditor reviews your documented policies, risk assessments, control implementations, and procedures to ensure they align with ISO 27001:2022 requirements. This audit helps to identify any gaps or issues before moving to the next phase.
Stage 2 – Implementation and Effectiveness Audit
Once the documentation is verified, the second stage checks how well your ISMS is functioning in practice. Auditors will interview staff, observe operations, and evaluate records to confirm that controls are working and that your team is following the documented procedures consistently.
After successfully completing both stages, your organization is issued an ISO 27001:2022 certification, valid for three years, with annual surveillance audits to ensure ongoing compliance.
Surveillance and Recertification: Throughout the three-year cycle, surveillance audits (annually) will be conducted by the certification body to ensure that your ISMS continues to operate effectively and that you are maintaining compliance.
Recertification audit is required to renew your ISO 27001 certification for the next cycle. The ongoing audits encourage organizations to continuously improve their security posture and not lapse into complacency.
How Pacific Certifications Can Help?
Selecting the right certification partner is crucial to a smooth and valuable ISO 27001 certification experience. We at Pacific Certifications distinguish us as an ideal choice for organizations worldwide seeking ISO 27001:2022 certification. We provide:
- Stage 1 and Stage 2 certification audits
- Evaluation of Annex A control implementation
- Statement of Applicability (SoA) review
- Support for integrated audits (ISO 27001 + ISO 27701 + ISO 9001 etc.)
- Annual surveillance audits and recertification audits every 3 years
- Objective, impartial certification without providing consultancy
If you are looking for ISO/IEC 27001:2022 certification, contact us at support@pacificcert.com
FAQs – ISO 27001:2022
What is ISO 27001?
ISO 27001 is the globally recognized management-system standard for information security. It sets requirements for identifying risks, selecting controls, and running an ongoing program that keeps data safe and available.
Is ISO/IEC 27001:2022 mandatory?
No, but it is often contractually required by clients and regulators, especially in IT, finance, and healthcare sectors.
What are the key updates in the 2022 version?
The most significant change is the restructuring of Annex A controls from 114 to 93 controls across 4 themes, aligning with ISO/IEC 27002:2022.
How long is ISO/IEC 27001 certification valid?
The certificate is valid for 3 years, with annual surveillance audits and recertification in the third year.
Can ISO 27001 be integrated with other standards?
Yes. It is commonly integrated with ISO 9001 (quality), ISO 27701 (privacy), ISO 22301 (BCMS), and ISO/IEC 27018 (cloud PII protection).
Is ISO/IEC 27001 suitable for small businesses?
Absolutely. ISO/IEC 27001 is scalable and can be tailored to fit small and medium-sized enterprises.
How do you get ISO 27001 certification?
Map your current security practices against the standard, close the gaps, run internal audits and a management review, then invite an accredited certification body for a two-stage external audit. When all findings are resolved the body issues the certificate, valid for three years.
How much does ISO 27001 certification cost?
Budgets vary with head-count, number of sites, and the audit days needed. Small firms often spend USD 10 000–30 000 across preparation, the initial audit, and the first year of surveillance. Larger or multi-site operations pay more.
Who needs ISO 27001?
Any organization that stores, processes, or transmits sensitive information—such as tech providers, financial firms, healthcare services, and government contractors—can use the certificate to prove that its security program meets an accepted international benchmark.
How do you maintain ISO 27001 certification?
Keep risk assessments current, review controls, run internal audits, hold at least one management review each year, and host annual surveillance visits from your certification body. Continual improvement is expected throughout the three-year cycle.
What is an ISO 27001 audit?
It is a formal review carried out by an accredited auditor who checks documents, interviews staff, and samples evidence to confirm that the information-security management system meets every clause and control set required by the standards.
Ready to get ISO 27001:2022 certified?
Contact Pacific Certifications to begin your certification journey today!
Suggested Certifications –
Read more: Pacific Blogs






